TechInAfrica – You may have seen our previous story about WhatsApp and Telegram and their risk of hacking. In summary, files shared via these apps are at risk of being exposed and manipulated by ‘malicious actors’ if particular features are enabled. This phenomenon is often regarded as Media File Jacking—yet some people are still oblivious on how does it exactly work. Do not fret, as we are once again here to address your confusions!
Cited from Symantec’s official blog, the company in charge of Norton explained briefly about Media File Jacking:
It stems from the lapse in time between when media files received through the apps are written to the disk, and when they are loaded in the apps’ chat user interface (UI) for users to consume. This critical time lapse presents an opportunity for malicious actors to intervene and manipulate media files without the user’s knowledge.
Such security flaw allows the opportunity for hackers to exploit and manifest these glitches in order to alter, misuse, or manipulate information for the recipient. Documents in risk of alteration involve photos, videos, invoices, or even voice recordings. This, in return, would jeopardize the trust between both the sender and the recipient—most often between coworkers, stakeholders, or companies in general—in order for the malicious to achieve personal gain (or simply to wreak havoc. Yikes.)
Take a look at the video below to understand how it works:
I guess you can’t take that Face Off—see what I did there?
However, this brings us to a deeper point of exposition. The common perception of the common people defines that the newest instant messaging services are flawlessly protected by end-to-end encryption systems. Well, that’s not entirely wrong—but that’s not entirely true either—while it’s a must for the referred services to manifest the newest encryption mechanisms to further ensure the sustainability for its users, it’s not exactly ‘flawless’, as we had so eloquently put it.
Symantec stressed that:
However, as we’ve mentioned in the past, no code is immune to security vulnerabilities.
Yes, it’s definitely more secure than SMS—which can be easily spoofed, but its defense is not impenetrable. Attackers are still bound to find logical flaws in the code and exploit it to their heart’s content; more than often it happens real-time and real fast, too.
So, how do the attacks work exactly?
Mainly, instant messaging users store their data in their phones’ external storage due to of a number of reasons. Primarily because external storage is less complicated and often offers up more space in comparison to internal storage. This is where the hackers are provided the most substantial opportunity. As tempting as ‘more space’ sounds, files saved in the external storage is free to be accessed by several other applications—even those of irrelevance. Contrary to the files saved in the internal storage, which can only be accessed to the corresponding, exclusive apps.
An Android developer post explained us:
External storage is the best place for files that don’t require access restrictions and for files that you want to share with other apps or allow the user to access with a computer. Internal storage is best when you want to be sure that neither the user nor other apps can access your files.
Files received via WhatsApp—and Telegram—are naturally stored in external storage directories, which makes them more vulnerable to attacks coming from unwanted, malicious malware. This also allows apps with write-to-external storage permission to overwrite and eventually alter sensitive documents saved in the external storage.
A research conducted by Symantec uncovered what the steps of the attacks are. To put it simply, with how similar media files are handled on WhatsApp and Telegram, files are first stored on the device without the users being able to see it. WhatsApp and Telegram (or any instant messaging platform) then fetches the file in order for the users to observe it—and this is where the file would be overwritten by the malware so that it’s modified from the sender’s initial purposes.
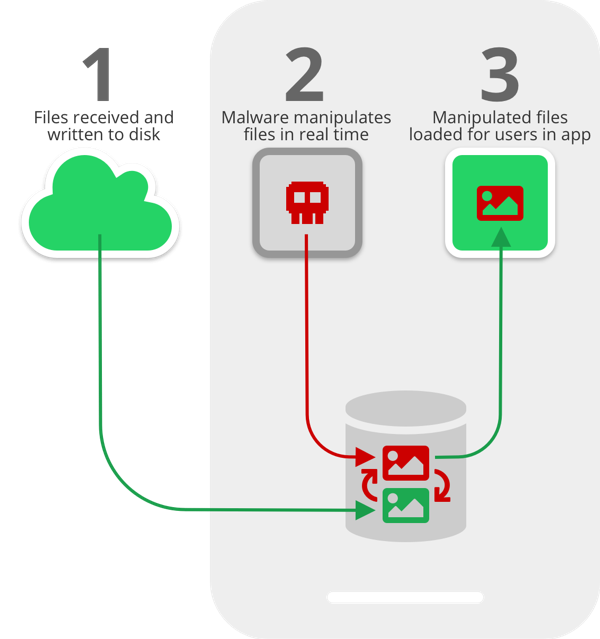
In other words, recipients will be delivered the altered files before they could even take a glimpse at the originals. The originals are still there in their phones somewhere, except that it has been overwritten by a false copy.
How do we prevent that from happening?
For one, users are strongly advised not to mindlessly click through the permissions whenever they install new apps. Permissions are fatal in regards to the owner’s security in general. Apps that requests aggressive permissions such as critical device sensors and resources access are most likely malicious—why would a shopping app have the urgency to access my fingerprint sensors? Totally hate it when they ask absurd things.
As we had mentioned in our post earlier this week:
Additionally, background usage of apps can also be a clear indicator that certain apps are most likely doing what they’re not supposed to. Rapid battery drain and high network data usage can be the parameters used to monitor your phone’s activities.
Or, you can simply set up your settings so that files are automatically stored in the internal storage. Some instant messaging platforms have also manifested this method in order to protect its files’ integrity.
Aside from photos, invoices and audio files can also be altered—with the former specifically designed to benefit the hacker personally. Take a look at the two videos below:
Okay, you gotta admit Willy Wonka is such an awkward name for a hacker. How about JB Markowicz, for example?
All in all, it all comes down to the users to protect their own files. We believe that instant messaging giants like WhatsApp and Telegram have already implemented cutting-edge security measures, but it’s all for naught if the users are still oblivious to the threats of the digital world.
Source: symantec.com