TechInAfrica – They say keep your friends close and your enemies closer. If we pry behind the logic of this proverb, it’s best not to only depend on your antivirus and firewall protection software, but also to know what kinds of threats are lurking in the cyberspace. ESET, an internet security company, recently highlighted five of the most malicious malwares of this year—with hopes that internet users would be more wary in taking steps while surfing the web.
Here are five of the most dangerous viruses discovered in 2019:
Machete
Machete, a malware that has been used in cyberespionage operations primarily in Venezuela, Ecuador, Colombia, and Nicaragua, is mainly used for spear-phishing government institutions with the malicious goal to steal a country’s most classified data and documents.
Cited from Kaspersky’s official website, the antivirus developer defines spear-phishing as an email or electronic communications scam targeted towards a specific individual, organization or business. For example, the FBI has warned of spear phishing scams where the emails appeared to be from the National Center for Missing and Exploited Children.
Once the victim falls to the trick, the malware then collects keystrokes, accesses the clipboard, takes screenshots, and retrieves confidential files to be presented to the operator. Despite mainly targeting government organizations, Machete can still be used to target personal internet users like you and me. Yikes!
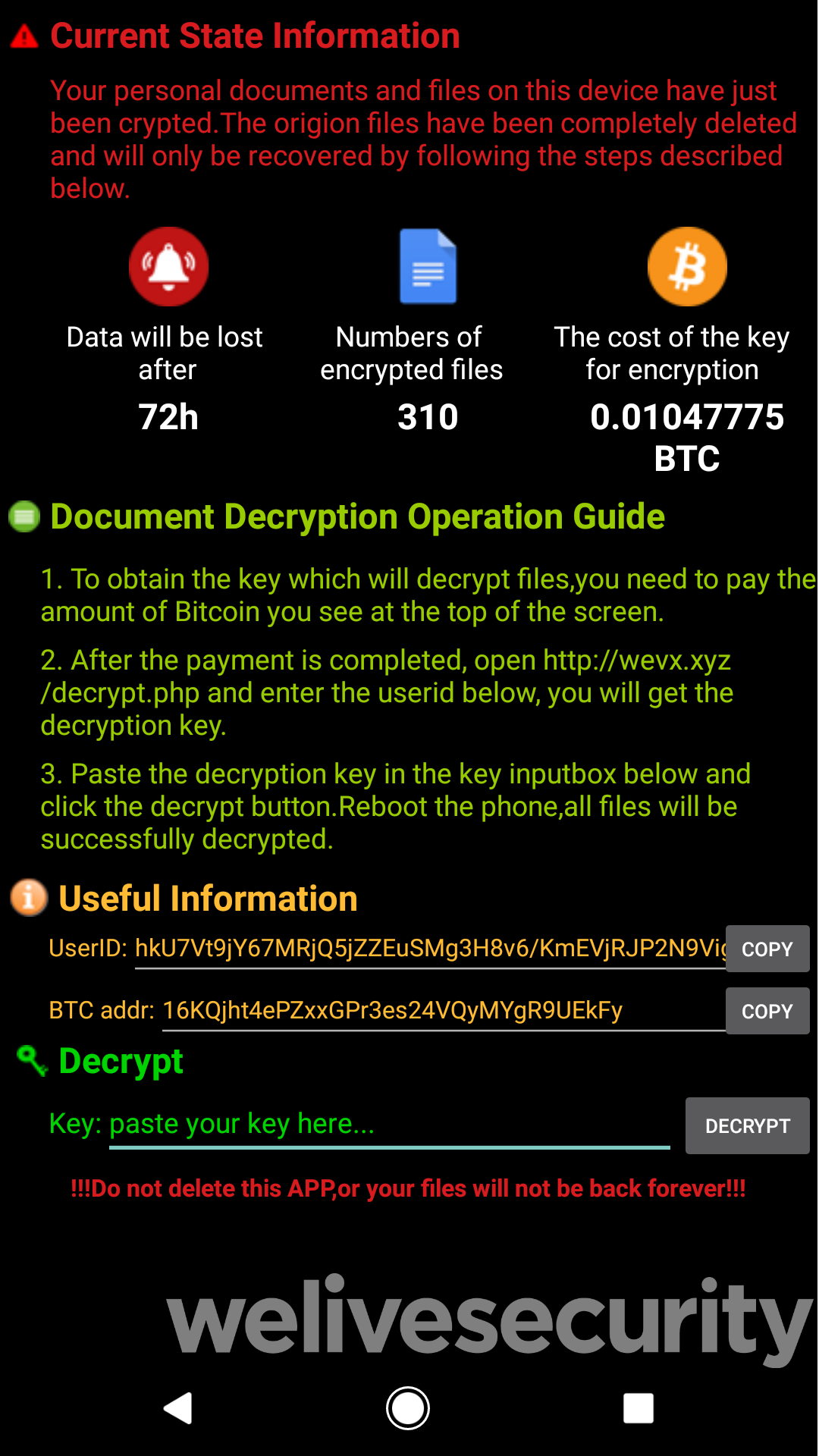
Android/Filecoder.C
Android/Filecoder.C, targeting Android mobile devices, is a ransomware that encrypts the user’s data before asking for a fee (in Bitcoin) for its decryption. Distributed via online forums, these malware files have the capacity to not only encrypt files but to also send text messages to the victim’s contact list. Refer to the screenshot below to see what the virus looks like:
Android/FakeApp.KP
Yet again another malware targeting Android mobile devices, this one is used to phish for login credentials to BtcTurk, a Turkish cryptocurrency exchange. The site uses Google’s two-factor authentication service which allows users to obtain a one-time password through SMS. Instead of intercepting the SMS (which became harder due to Google’s new restrictions), the malware ‘reads’ the SMS itself to obtain the password before the users can do anything about it.
Varenyky
When it’s in the user’s computer, the Varenyky Virus may take screencaps or even record short videos of the user’s screen, if the target is visiting sites with adult content (porn sites, adult chat rooms, etc).
Any images, or video footage gathered by the Varenyky virus can then be used by the hackers to extort money from you via blackmailing. The criminals would probably threaten that they would upload the captured images/videos online, and/or send them to your contacts if you don’t pay a ransom to them. They may even send you some of the materials they’ve captured in order to prove to you that they aren’t simply trying to scam you.
KRACK for Wi-Fi devices
A devastating flaw in Wi-Fi’s WPA security protocol makes it possible for attackers to eavesdrop on your data when you connect to Wi-Fi.

Key Reinstallation Attacks, or KRACK, primarily targets Wi-Fi enabled devices, including Amazon Echo and at least one generation of Amazon Kindle. Via this malware, attackers can launch DDoS (Denial of Service) attacks to the victims. In addition, they can also disrupt network communications and intercept sensitive information such as passwords.
Fortunately, these threats are already able to be addressed by simply looking it up on Google—trust me, I’ve done so—or by installing the latest updates of your antivirus. Then again, this doesn’t mean that there are no bigger threats lurking out there in the web; we just haven’t found them yet.
So, set up countermeasures the next time you dive towards the internet to ensure you (and your data)’s security—you’ll never know what you’ll be up against.
Source: itnewsafrica.com





